Agent Routing Architecture: Why Small Agents Are Better Than Smart Ones
Agents under 150 lines that route to specialized skills. Identity and routing, not implementation.
What if your AI knew exactly which expert to call—every time?
Ask a general AI to "run a pentest" and you get generic advice. Ask Intelligence Adjacent and you get a security agent loading PTES methodology, creating engagement directories, and executing domain-specific workflows.
The difference isn't model intelligence. It's architectural routing—the pattern Anthropic calls "orchestration over intelligence."
The Problem: Jack of All Trades
Think of it like calling a company switchboard. A switchboard that tries to answer every question itself fails quickly. Questions about billing, technical support, sales—they all need different expertise.
Most AI frameworks are broken switchboards. They try to handle everything with one generalist. Sometimes it works. Often it doesn't.
Agents are the switchboard that routes correctly.
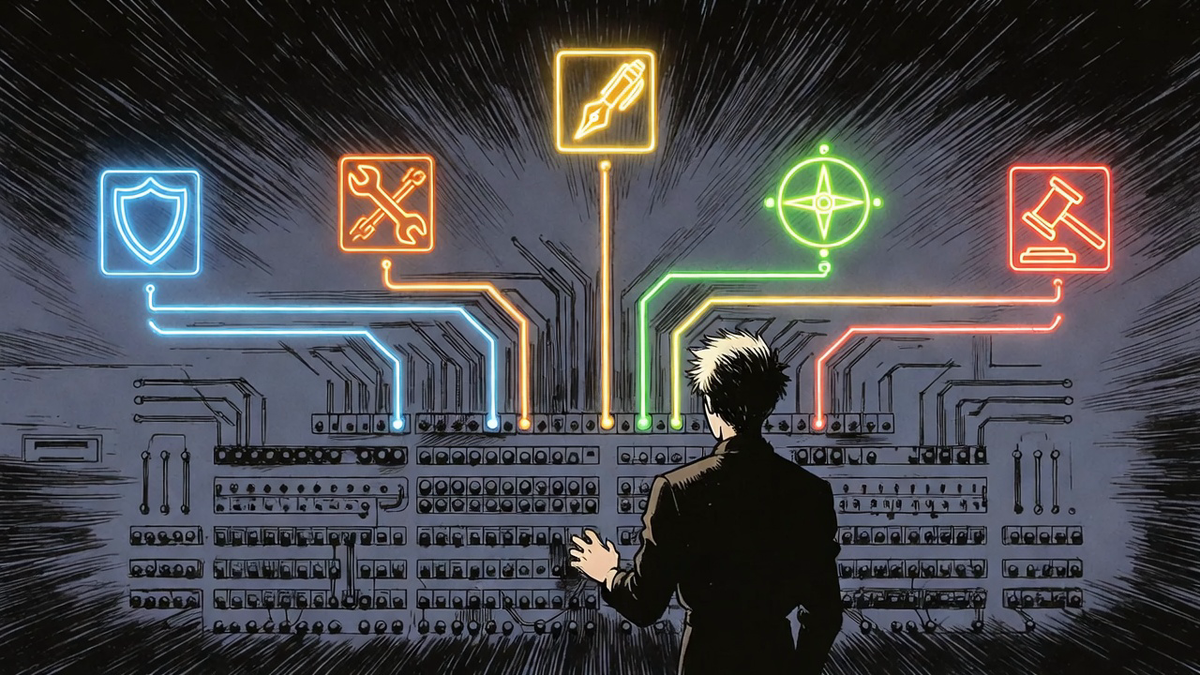
Security question? Route to security agent. Blog post? Route to writer agent. Career advice? Route to advisor agent. Legal compliance? Route to legal agent.
Each agent knows its domain. Each agent loads the right skills.
The Solution: Thin Wrappers
Agents in Intelligence Adjacent are intentionally small—under 150 lines each. This isn't arbitrary constraint. It's architectural discipline.
What agents contain:
- Identity (who am I, what's my expertise)
- Routing rules (which skills for which tasks)
- Startup sequence (what to load)
- Operational requirements (mandatory steps)
- Output standards (how to format results)
What agents DON'T contain:
- Complete methodologies (those live in skills)
- Tool implementations (those live in scripts)
- Reference materials (those load on-demand)
An agent is a router, not an encyclopedia.
The Agents
The framework has five specialized agents, each routing to relevant skills for their domain. For complete skill listings and commands, see the IA Framework Reference.
Security Agent
Domain: Offensive testing + defensive advisory
Routes to security-focused skills including pentesting, code review, threat intelligence, vulnerability assessment, and incident response workflows.
Key capability: Three engagement modes—Director (autonomous production), Mentor (learning with explanations), Demo (controlled testing).
Mandatory requirement: Authorization verification before any testing. SCOPE.md = Authorization.
Engineer Agent
Domain: Implementation and remediation
Routes to implementation skills for security fixes, infrastructure changes, and hardening configurations.
Key capability: SSH-first execution model—works anywhere with SSH access. Turns security findings into actual fixes.
Mandatory requirement: Plan mode required. Rollback plan mandatory before any production changes. Verification-driven.
Core distinction: Security agent FINDS issues. Engineer agent FIXES issues.
Writer Agent
Domain: Content creation across formats
Routes to content skills including blog writing, documentation, diagram generation, and Ghost CMS publishing.
Key capability: QA enforcement—rating must hit 5/5 before staging. Delegates to qa-review skill automatically.
Mandatory requirement: Load content-guardian prompt before blog/docs work (no hardcoded counts).
Advisor Agent
Domain: Personal development + research + compliance
Routes to advisory skills including career development, fitness programming, compliance assessments, and research workflows.
Key capability: GO/NO-GO filtering—rejects poor job matches in under 5 minutes, saving hours on dead ends.
Mandatory requirement: Evidence-based recommendations only. Never fabricate sources or experience.
Legal Agent
Domain: Legal compliance (NOT legal advice)
Routes to legal skill for HIPAA, PCI DSS, GDPR, and contract review.
Key capability: Mandatory citation verification—every case citation and statute verified via WebSearch before presenting.
Mandatory requirement: Disclaimer on every response. Attorney consultation recommended.
How Routing Works
When you invoke an agent, the framework loads context in layers. First, base Claude determines which agent should handle the request:
┌──────────────────────────────────────────────────────────┐
│ USER REQUEST │
└──────────────────────────────────────────────────────────┘
↓
┌──────────────────────────────────────────────────────────┐
│ Base Claude (Orchestrator) │
└──────────────────────────────────────────────────────────┘
↓
┌───────────────┴───────────────┐
│ Routing Decision Tree │
└───────────────┬───────────────┘
↓
┌────────────────────┼────────────────────┐
│ │ │
┌───▼────┐ ┌───────▼───────┐ ┌────▼─────┐
│ Basic │ │ Specialized │ │ Multiple │
│ File/ │ │ Domain Work? │ │ Tasks │
│ Git │ │ │ │ (3+) │
│ Ops? │ │ │ │ │
└───┬────┘ └───────┬───────┘ └────┬─────┘
│ │ │
↓ YES ↓ YES ↓ YES
Handle Route to Agent Spawn Parallel
Directly Agents
│ │
│ ┌──────────┼──────────┬──────────┬──────────┐
│ │ │ │ │ │
│ ┌────▼───┐ ┌───▼────┐ ┌──▼─────┐ ┌──▼─────┐ ┌──▼─────┐
│ │Security│ │Engineer│ │Writer │ │Advisor │ │Legal │
│ │Testing │ │Implem- │ │Content │ │Research│ │Compli- │
│ │Vuln │ │entation│ │Blog │ │Career │ │ance │
│ │Review │ │Harden │ │Docs │ │OSINT │ │GDPR │
│ └────────┘ └────────┘ └────────┘ └────────┘ └────────┘
│ │ │ │ │ │
└─────────┴──────────┴──────────┴──────────┴──────────┘
↓
Load Agent Context + Skill
↓
Execute Workflow
↓
Return Results
Once the appropriate agent is selected, it loads its context and executes the skill workflow:
┌──────────────────────────────────────────────────────────┐
│ USER: "Analyze this job posting" │
└──────────────────────────────────────────────────────────┘
↓
┌──────────────────────────────────────────────────────────┐
│ BASE CLAUDE (Orchestrator) │
│ Detects: career-related keywords │
│ Routes to: advisor agent │
└──────────────────────────────────────────────────────────┘
↓
┌──────────────────────────────────────────────────────────┐
│ ADVISOR AGENT │
│ Loads: agents/advisor.md (~2K tokens) │
│ Loads: skills/career/SKILL.md (~15K tokens) │
└──────────────────────────────────────────────────────────┘
↓
┌──────────────────────────────────────────────────────────┐
│ CAREER SKILL WORKFLOW │
│ Phase 1: GO/NO-GO (~8K tokens, Haiku) │
│ ├─ Score match: 72/100 │
│ └─ Decision: PROCEED │
│ Phase 2: RESEARCH (~15K tokens, Haiku + Web) │
│ Phase 3: PREPARE (~18K tokens, Sonnet) │
│ Phase 4: GENERATE (~22K tokens, Sonnet) │
│ Phase 5: DELIVER (~2K tokens, Haiku) │
└──────────────────────────────────────────────────────────┘
↓
┌──────────────────────────────────────────────────────────┐
│ OUTPUT: Complete Package (6 files) │
│ Total tokens: ~65K ≈ 10 min Claude Pro daily usage │
└──────────────────────────────────────────────────────────┘
Token Breakdown:
- Context loading (agent + skill): ~17K tokens (one-time per session)
- Workflow execution: 8K-65K tokens (depending on GO/NO-GO gates)
- Total for full analysis: ~65K tokens ≈ 10 minutes of Claude Pro daily usage
The agent doesn't contain the career methodology. It routes to the skill that does. This separation keeps agents under 150 lines while allowing skills to contain complete, production-grade workflows.
This separation means:
- Agents stay small (under 150 lines)
- Skills can be updated independently
- Multiple agents can share skills (osint-research is used by career, security-testing, and writer)
- Adding new skills doesn't require agent changes
The 150-Line Limit
Every agent must be under 150 lines. A pre-commit hook enforces this.
Why? Because agents that grow beyond this threshold are doing too much. They're trying to contain expertise instead of routing to it.
When an agent approaches 150 lines:
- Extract methodology to a SKILL.md file
- Reference instead of inlining
- The agent becomes a pointer, not a container
The constraint forces good architecture. Agents route. Skills implement. References provide detail.
Agent Format
Every agent follows the same structure:
---
type: agent
name: security
description: "[security:sonnet] Unified security agent..."
model: sonnet
---
# Security Agent
## Quick Start
Auto-load skill, decision tree pattern, engagement modes
## Core Identity
Who you are, what you do, key capabilities
## Mandatory Startup Sequence
Load framework → Load catalog → Load skill → Execute
## Operational Requirements
Authorization, workflow pattern, session tracking
## Output Standards
Finding documentation, deliverable formats, severity
## Critical Reminders
Ethical boundaries, scope compliance, completion tag
The template ensures consistency. Learn one agent, understand all agents.
Multi-Agent Routing
Some tasks need multiple agents. The framework handles this through delegation.
Example: Security assessment with legal review
- User requests comprehensive security assessment
- Security agent executes testing methodology
- Security agent identifies compliance findings
- Security agent delegates legal review to legal agent
- Legal agent verifies regulatory requirements
- Combined deliverable returned
The agents don't merge. They collaborate, each maintaining their specialization.
Token Economics: Why Model Routing Matters
Smart agent routing isn't just about accuracy—it's about token efficiency. By routing to the right model at the right time, the framework optimizes for both quality and cost.
Example: Career Analysis Workflow
Without model routing (Sonnet-only):
- All phases use Sonnet 4.5 (expensive, powerful)
- Phase 1 (screening): 12K tokens (overkill for pattern matching)
- Phase 2 (research): 20K tokens (unnecessary for data aggregation)
- Phase 3-5: 50K tokens (appropriate for strategic thinking)
- Total: ~82K tokens ≈ 13 minutes of Claude Pro daily usage
With smart routing (Haiku + Sonnet):
- Phase 1 (screening): 8K tokens Haiku (optimal for scoring)
- Phase 2 (research): 15K tokens Haiku (sufficient for data gathering)
- Phase 3-4 (strategy + writing): 40K tokens Sonnet (appropriate for quality output)
- Phase 5 (delivery): 2K tokens Haiku (formatting only)
- Total: ~65K tokens ≈ 10 minutes of Claude Pro daily usage
Savings: ~20% token reduction with equivalent or better output quality. Over 40 job analyses per month, that's roughly 2 hours of Claude Pro usage saved—about 8-10% of monthly allocation.
Multi-Agent Workflows Scale Better:
Security assessment with legal review (two agents):
- Security agent: 80K tokens (Sonnet for deep analysis)
- Legal agent: 25K tokens (Haiku for citation verification)
- Total: 105K tokens ≈ 16 minutes of Claude Pro daily usage
Compare to single generalist model attempting both:
- No routing optimization
- Higher token usage for context switching
- Lower quality due to lack of specialized prompts
- Estimated: 140K+ tokens ≈ 22+ minutes of Claude Pro daily usage
The value of agent routing: appropriate model selection at each phase, reducing unnecessary token consumption while maintaining or improving quality.
Why This Matters
Agents embody the Intelligence Adjacent principle: orchestration over intelligence.
A smarter model doesn't automatically produce better pentests. A smarter model with PTES methodology, domain-specific tools, and structured workflows does.
Agents provide that structure. They ensure the right expertise handles the right tasks. They enforce standards that raw intelligence can't guarantee.
The value isn't in the agent itself. It's in the routing to specialized skills, the loading of proven methodologies, and the enforcement of professional standards.
Thin wrappers. Maximum routing. That's the agent architecture.
Related Posts
- IA Framework Architecture - How agents fit the system
- Skills as Expertise Modules - What agents route to
- Slash Commands Deep Dive - Commands that invoke agents
- VPS Server Tools - Tools agents use
Sources
Framework & Architecture
- IA Framework Repository - Full source code and agent implementations
- Building Effective Agents - Anthropic - Orchestration patterns and design principles
Claude Code Integration
- Claude Code Documentation - Official Claude Code reference
- Claude Code Skills - Skill system that agents route to
Security Methodologies Referenced
- PTES - Penetration Testing Execution Standard - Security testing methodology
- OWASP Testing Guide - Web application security
- MITRE ATT&CK - Adversary tactics and techniques
Don't Miss the Next Post
Subscribe for free to get updates on AI architecture and intelligent systems.